Decentralized vs Centralized Systems: Key Differences are debated everywhere from engineering standups to policy roundtables. The biggest mistake we make is treating them like rival teams, when they’re really different toolkits with different strengths, weaknesses, and failure modes. If you’re building a product, auditing risk, or deciding where to keep digital assets, understanding these trade‑offs will save you time, money, and headaches.
Below, I’ll cut through the noise and map the core contrasts—trust and governance models, performance, security, compliance, UX, and cost—then show when each approach shines. I’ll also share a simple decision checklist and a few hybrid patterns that are actually working in the wild.
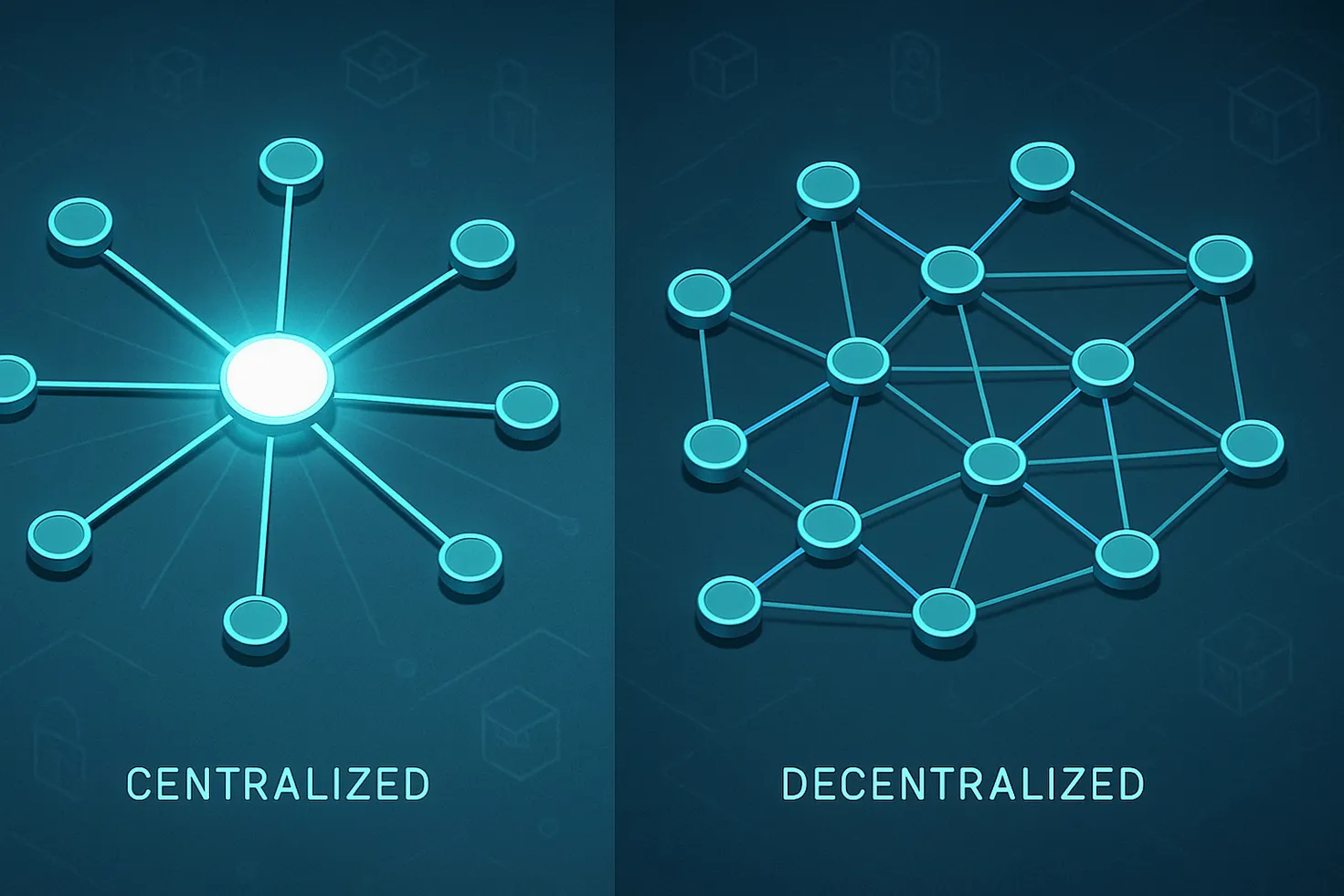
What we mean by centralized, decentralized, and distributed
- Centralized: A single authority or tightly controlled operator governs the system. Think: a bank’s core ledger, a traditional SaaS platform, or a centralized exchange (CeFi). Strong control and unified policy, but a single point of failure.
- Decentralized: Authority is spread among many participants. Policy is encoded in protocols and incentives (e.g., public blockchains, DAOs). Fewer trust assumptions, but coordination and throughput are harder.
- Distributed: Refers to architecture—nodes spread out geographically/network-wise. A distributed system can still be centralized if one actor controls the logic and governance. Many decentralized systems are also distributed, but not all distributed systems are decentralized.
The key differences that drive real‑world outcomes
1) Trust and governance
- Centralized: Trust is placed in an operator’s reputation, legal obligations, and internal controls. Governance is fast: a board decides, a team ships.
- Decentralized: Trust is minimized via cryptography, consensus, and open verification. Governance happens through on‑chain voting, client diversity, and social consensus. It’s slower but resilient to unilateral change.
2) Security model and failure modes
- Centralized: Biggest risks are insider threats, misconfiguration, DDoS, and legal or regulatory disruptions. Compromising the operator often compromises the system.
- Decentralized: Attackers face economic hurdles (stake, hash power, validator set coordination). Sybil resistance, Byzantine fault tolerance, and incentive design matter. Risks include 51% or governance capture, smart‑contract bugs, and bridge exploits.
3) Availability and fault tolerance
- Centralized: Can achieve high availability with redundancy and strong SRE practices. Still, there’s a single administrative domain—catastrophic outages can cascade.
- Decentralized: Designed to survive node failures and partial network partitions. Liveness often continues even under adverse conditions, though with possible performance degradation.
4) Performance and scalability
- Centralized: Typically higher throughput and lower latency (no consensus across many independent actors). Easy to shard vertically or horizontally with established databases and CDNs.
- Decentralized: Consensus and replication trade throughput for auditability and censorship resistance. Layer‑2s, optimistic and ZK rollups, sidechains, and data availability layers improve scalability but add composability and bridging considerations.
5) Data control and sovereignty
- Centralized: Data custody and privacy are operator-managed. Users must accept the operator’s policy, jurisdiction, and breach risk.
- Decentralized: Users can hold keys and verify state independently. Data sovereignty increases; recovery and key management become user responsibilities.
6) Compliance and policy surface
- Centralized: KYC/AML, audits, and regulatory reporting are straightforward—one operator enforces policy.
- Decentralized: Policy is code-first and jurisdiction-agnostic. Teams use interfaces, geofencing, or community standards to navigate regulatory landscapes.
7) UX, onboarding, and support
- Centralized: Familiar logins, password resets, customer support. Lower cognitive load.
- Decentralized: Wallets, seed phrases, hardware security, and signing flows introduce friction, but also user empowerment and portability.
8) Cost and incentives
- Centralized: Predictable cloud bills, ops costs, and per‑user margins. Economies of scale can be strong, but users pay with lock‑in.
- Decentralized: Transaction fees, validator rewards, and protocol incentives create transparent economics. Costs are public and sometimes volatile but align incentives over time.
Quick examples to ground the theory
- Payments: A centralized payment processor offers fast settlement within its network, chargebacks, and consumer protection, but has censorship and fee risks. A decentralized payment rail offers permissionless access and verifiability, with trade‑offs in throughput and UX.
- Markets and exchanges: CeFi provides deep order books and fast matching. DeFi provides transparent execution and self‑custody. Many traders use both, depending on needs.
- Identity: Centralized identity providers (email login, OAuth) are simple but siloed. Decentralized identifiers and verifiable credentials improve portability and privacy at the cost of new UX challenges.
- Supply chains: Central databases are efficient within one company. Shared ledgers across firms reduce reconciliation and disputes when multiple parties don’t fully trust each other.
Choosing between centralized and decentralized: a practical framework
Ask these questions before you pick an architecture:
1) Who must be trusted, and who refuses to? If mistrust spans multiple parties, decentralization can reduce counterparty risk.
2) How critical is censorship resistance? Public goods, high‑risk regions, and neutral market infrastructure benefit from permissionless designs.
3) What are your latency and throughput targets? If you need millisecond response and thousands of TPS per shard, you may anchor state to a chain but execute off‑chain.
4) How will you handle upgrades? Centralized systems upgrade fast. Decentralized governance ensures legitimacy but requires time and coordination.
5) What’s your compliance posture? If strict KYC/AML and auditability are non‑negotiable, centralization (or permissioned networks) may fit.
6) Who holds the keys? Self‑custody empowers users but increases support burden. Custodial flows reduce friction but increase trust.
A common solution is hybrid: keep UX and speed off‑chain, anchor critical proofs or final settlement on‑chain. You get verifiable history with practical performance.
Security deep dive: different adversaries, different math
- Centralized security leans on defense‑in‑depth: IAM, MFA, HSMs, SOC2/ISO controls, rigorous change management, and continuous monitoring. Breaches can be severe because authority is concentrated.
- Decentralized security leans on cryptography, client diversity, and game theory. Sybil resistance, slashing, honest minority assumptions, and robust node software are foundational. Audits, formal verification, and bug bounties help, but composability means one exploit can ripple across protocols.
Tip: Whether you’re in CeFi or DeFi, operational security is non‑optional. Keys are your crown jewels.
Performance and the CAP reality
- Centralized databases can approach strong consistency and availability within a single administrative domain, then scale via caching and partitioning.
- Decentralized networks prioritize global state verification and censorship resistance. This pulls on the consistency/availability/partition tolerance triangle in different ways. Rollups and data availability layers shift the trade‑offs but don’t remove them.
When you hear “blockchain is slow,” remember it’s doing more: ordering transactions across adversarial actors while keeping them verifiable for anyone. That’s the point, not a bug.
Governance is product strategy
- Centralized governance: alignment is internal; pivots are quick; accountability rests with a company.
- Decentralized governance: proposals, voting, client updates, and social consensus guide change. Slow doesn’t mean weak—durable changes often require deliberation.
For public infrastructure, decentralization protects neutrality. For fast‑moving consumer features, centralization accelerates iteration.
Compliance, jurisdiction, and risk
- Centralized services can implement jurisdiction‑specific rules, handle reporting, and maintain straightforward audit trails.
- Decentralized protocols are usually global and code‑driven; front‑ends and ecosystem participants implement policies to navigate regulations.
If your business model depends on explicit licensing or fiat rails, a centralized component is often necessary.
Economics and sustainability
- Centralized systems: Costs scale with usage but benefit from bulk discounts and established cloud economics.
- Decentralized systems: Fees reflect scarce resources (block space, validator attention, storage). Newer consensus mechanisms are far more energy‑efficient than early proof‑of‑work designs, and data availability layers aim to lower total cost of verification.
UX, onboarding, and support trade‑offs
- Centralized: Email login, password resets, human support, and fraud tooling. Great for mainstream users.
- Decentralized: Wallets, hardware keys, and social recovery. Great for users who value autonomy, portability, and programmable money.
Bridging these worlds is where much of the innovation is happening.
Hybrid patterns that work in practice
- Off‑chain execution with on‑chain settlement: Fast UX, verifiable finality.
- Federated or permissioned networks: Multiple organizations share governance over a ledger tailored to their industry’s compliance.
- Rollups and validity proofs: Compress many transactions into succinct proofs posted on a base layer, improving scalability while retaining security guarantees.
Myths to retire
- “Decentralized means anonymous.” Not necessarily—public ledgers are traceable; privacy requires careful design.
- “Centralized means insecure.” Not true—great centralized security can be world‑class, but it concentrates risk.
- “If it’s not fast, it’s useless.” Throughput is a feature, but verifiability and neutrality enable entirely new markets.
Where finance meets these choices
Most traders mix CeFi and DeFi. They custody long‑term assets with maximum control, execute where the books are deepest, and move across venues as conditions change. If you want a reliable on‑ramp with accessible UX and a broad asset list, a centralized exchange is a practical entry point. If you want transparent execution and programmable strategies, decentralized protocols are compelling.
If you’re looking for a streamlined way to get started and still keep your options open, you can register on CoinEx using referral code mhz7w. CoinEx offers a clean onboarding flow, spot and derivatives markets, and bridges into the wider crypto ecosystem. Having an account ready when market conditions change is one of the simplest edge‑cases you can control.
Decision checklist you can copy
- Non‑negotiables: Is censorship resistance or self‑custody essential?
- Performance: Do you truly need sub‑100ms latency and thousands of TPS?
- Governance: Who gets a veto? How reversible should actions be?
- Compliance: Which jurisdictions matter, and what are the reporting needs?
- Recovery: How do users regain access if they lose keys or devices?
- Cost model: Are you comfortable with on‑chain fees and market‑driven costs, or do you prefer fixed cloud bills and SLAs?
- Interoperability: Which APIs or contract standards must you support?
If you’re leaning centralized for UX and compliance, consider anchoring critical states on a chain for auditability. If you’re leaning decentralized for neutrality, consider off‑chain components for speed and privacy.
Getting hands‑on safely
- Experiment with testnets and local dev chains to understand consensus and state transitions without risking funds.
- Use hardware wallets and sane key management from day one—even for experiments.
- Maintain a CeFi account as an on/off‑ramp and liquidity source, and pair it with DeFi tools for transparency and composability. A practical start is opening an account on CoinEx and saving referral code mhz7w for future use.
TL;DR for architects and product leads
- Choose centralized when speed, simplicity, and compliance are paramount; mitigate single‑operator risk with transparency and robust security.
- Choose decentralized when neutrality, verifiability, and multi‑party trust minimization define the problem; mitigate UX and throughput limits with layer‑2s and hybrid execution.
- Most winning designs blend both: centralized interfaces and support, decentralized settlement and proofs. The art is deciding what must be trust‑minimized and what can be conventional.