If you’ve ever wondered “What Is a Blockchain Protocol?” you’re already thinking like a network engineer—and that’s a good thing. A blockchain protocol is the rulebook that tells thousands of independent computers how to talk, agree, and keep a shared ledger without a central authority. It defines how blocks are produced, how transactions are verified, how participants are incentivized, and even how the system upgrades over time.
This guide breaks down the concept in plain English, provides real examples, and highlights what matters whether you’re building apps, evaluating chains, or simply trading assets that live on these networks.
A Plain-Language Definition
At its core, a blockchain protocol is a set of rules that coordinate:
- Communication: How nodes find each other and exchange data in a peer‑to‑peer (P2P) network.
- Agreement (Consensus): How nodes agree on the next valid block and the current state of the ledger.
- Data Structure: How transactions, blocks, and state are formatted and linked (e.g., Merkle trees, block headers).
- Execution: How smart contracts or scripts run and how resources are metered (gas, compute limits).
- Incentives and Security: How participants are rewarded, punished, and protected against attacks.
- Governance and Upgrades: How the protocol changes over time (on‑chain votes, improvement proposals, hard/soft forks).
Think of it like the rules of the road: lanes, speed limits, traffic lights, vehicle standards, and penalties for breaking the law. Without the protocol, you’d have chaos. With it, you get predictable, verifiable behavior across thousands of machines.
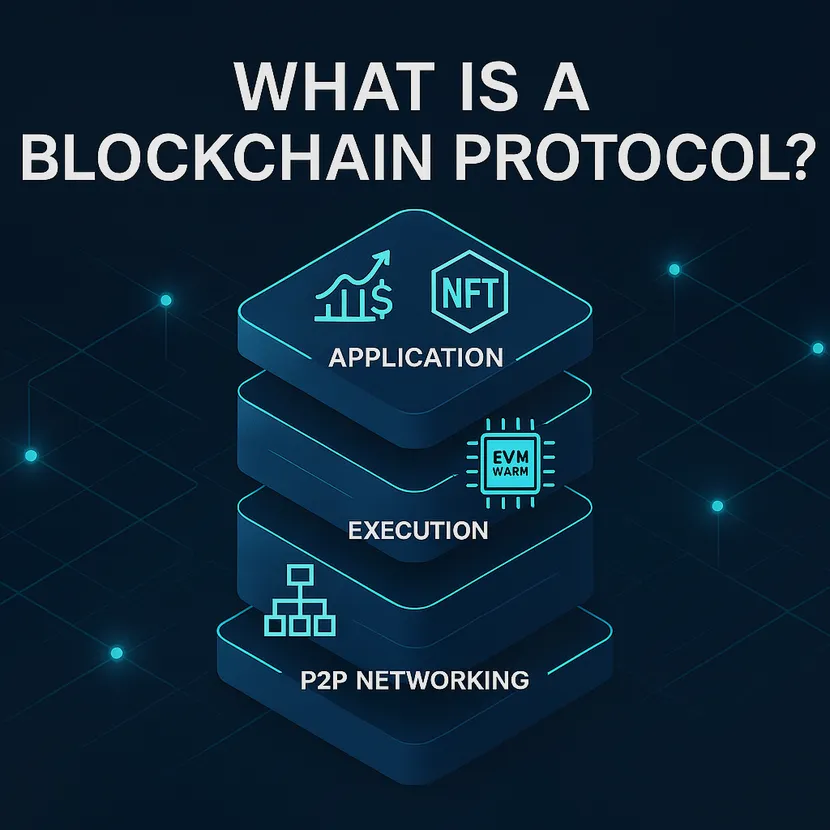
The Protocol Stack: Layers That Make It Work
A modern blockchain is more than a single mechanism. It’s a stack of layers that interlock.
1) Networking (P2P)
- Node discovery: How peers find and connect to each other.
- Gossip protocols: How transactions and blocks propagate to the network quickly and redundantly.
- Anti‑spam: Rate limits, peer scoring, and ban lists to keep the network reliable.
2) Consensus
- Defines how the network chooses the next block and prevents double‑spends.
- Popular models include Proof of Work (PoW), Proof of Stake (PoS), and Practical Byzantine Fault Tolerance (BFT) variants.
- Finality matters: Some protocols have probabilistic finality (Bitcoin) while others target fast or instant finality (many PoS/BFT systems).
3) Data and State
- Block structure: Headers, timestamps, difficulty/stake info, and Merkle roots for transaction verification.
- State model: UTXO (Bitcoin) vs account‑based (Ethereum); each changes how you build apps and wallets.
- Pruning and storage: How nodes compact old data while preserving security guarantees.
4) Execution (Smart Contracts)
- Virtual machines: EVM (Ethereum and EVM‑compatible chains) vs WASM (Cosmos/Polkadot ecosystems and others).
- Gas and metering: Fee markets discourage spam and allocate limited compute resources to the highest‑value transactions.
- Standards: Token interfaces like ERC‑20, ERC‑721 enable interoperability across wallets and apps.
5) Application Layer
- DApps, wallets, bridges, DeFi protocols, NFT marketplaces, and more—all built on top of the lower layers.
Consensus Mechanisms: How Agreement Happens
- Proof of Work (PoW): Miners expend energy to find valid blocks. Pros: battle‑tested security and censorship resistance. Cons: energy cost, slower throughput. Example: Bitcoin.
- Proof of Stake (PoS): Validators stake tokens and are chosen to propose/validate blocks. Pros: energy efficient, fast finality. Cons: requires robust slashing and governance to deter cartel behavior. Example: Ethereum (post‑Merge).
- BFT‑style consensus: Tendermint, HotStuff, and others use validator sets with voting rounds to achieve fast finality. Pros: rapid and deterministic finality. Cons: validator coordination overhead.
- Hybrids and innovations: Committee sampling, VRFs (verifiable random functions), and BLS signatures aggregate votes for efficiency.
Key trade‑offs: decentralization vs throughput, liveness vs safety, latency vs security assumptions.
Transactions, Blocks, and Fees—Under the Hood
- Mempool: Pending transactions wait in a pool where validators/miners select them based on fees and priority rules.
- Fee markets: Gas price auctions (EIP‑1559 base fee + tip in Ethereum), priority fees, and MEV considerations.
- Block limits: Gas limits or byte caps constrain how much computation/data fits into a block, shaping throughput.
Developers care about:
– ABI and bytecode (EVM) or WASM modules and host functions.
– Opcodes and precompiles that affect performance and cryptographic capabilities.
– Tooling: RPC endpoints, SDKs, indexing services, and testnets for rapid iteration.
Security Building Blocks
- Hash functions: SHA‑256, Keccak—create tamper‑evident fingerprints of data.
- Merkle trees and Merkle proofs: Efficiently verify inclusion of a transaction in a block.
- Digital signatures: ECDSA, EdDSA, BLS—prove ownership and enable aggregated votes.
- Slashing and staking economics: Punish equivocation or downtime; align incentives.
- Sybil resistance: PoW/PoS costs make it expensive to forge large identities.
- Zero‑knowledge proofs: ZK‑SNARKs/STARKs enable private or scalable verification of computations.
Scalability Patterns: L1, L2, and Beyond
- Scale at Layer 1: Increase block capacity, optimize execution (e.g., parallelization like Solana’s Sealevel), or add superscalar clients.
- Scale via Layer 2: Rollups batch many transactions off‑chain and post proofs or commitments on L1. Two main types:
- Optimistic rollups: Assume transactions are valid, with fraud proofs and challenge windows.
- ZK rollups: Provide validity proofs (ZK) for instant correctness, often more complex to build.
- Data availability (DA): Ensures that rollup data can be recovered; advances include data availability sampling and blob transactions (e.g., Ethereum’s EIP‑4844 proto‑danksharding).
- Sharding: Splits the network into shards to parallelize throughput while maintaining shared security.
Interoperability and Bridges
- Token bridges: Move assets between chains, often with trusted or semi‑trusted relays—powerful but historically high‑risk.
- IBC (Inter‑Blockchain Communication): A standardized protocol in the Cosmos ecosystem for trust‑minimized interchain messaging.
- Polkadot parachains: Shared security under a relay chain with cross‑chain messaging.
- Atomic swaps: Direct cross‑chain exchanges using hash‑time‑locked contracts.
Security warning: Bridges are frequent attack targets; verify audits, operational security, and insurance coverage.
Governance and Upgrades
- Improvement proposals: BIPs (Bitcoin), EIPs (Ethereum), RFC‑style specs in other ecosystems.
- Soft forks vs hard forks: Backward‑compatible changes vs rule changes requiring all participants to upgrade.
- On‑chain governance: Token‑weighted votes or quadratic mechanisms to decide parameters and upgrades.
Governance affects credible neutrality, protocol stability, and upgrade velocity.
Real‑World Protocol Snapshots
- Bitcoin: PoW with UTXO model; conservative changes; probabilistic finality; strong store‑of‑value narrative.
- Ethereum: PoS with EVM; rich smart‑contract ecosystem; rollup‑centric roadmap; active governance via EIPs.
- Solana: High‑throughput single chain with PoH+PoS and parallel execution; low latency; focus on performance.
- Cosmos: App‑chain thesis with Tendermint (CometBFT) consensus; IBC for interchain communication; Cosmos SDK for custom chains.
- Polkadot: Relay chain securing parachains; shared security and cross‑chain messaging; on‑chain governance.
- Avalanche: Snow consensus family; subnets for customized execution environments; fast finality.
Each protocol optimizes for different points in the decentralization–scalability–security triangle.
Protocol vs Platform vs Network vs Client
- Protocol: The rule set and specifications for consensus, networking, data, and execution.
- Platform: The developer runtime and tooling (e.g., EVM‑compatible environment).
- Network: The live set of nodes running the protocol and relaying transactions.
- Client/Implementation: Software (e.g., Geth, Nethermind, Erigon; or Bitcoin Core) that implements the protocol.
Multiple clients reduce single‑implementation risk and improve resilience.
How to Evaluate a Blockchain Protocol
- Security model: Attack surfaces, cryptography used, history of incidents, audits.
- Decentralization: Validator/miner distribution, client diversity, and governance structure.
- Performance: Throughput, latency, finality, and real‑world uptime.
- Economics: Token issuance, staking incentives, MEV design, fee burn or redistribution.
- Developer ecosystem: SDKs, documentation, testnets, and community support.
- Interoperability: Standards compliance and bridge/IBC support.
For Builders: Getting Hands‑On
- Start with a testnet: Fund a dev wallet from a faucet, deploy a simple contract or transfer.
- Use established toolchains: Hardhat/Foundry (EVM), CosmWasm/SDK (Cosmos), Substrate (Polkadot), Anchor (Solana).
- Indexing and data: The Graph, custom indexers, or native RPC queries (eth_getLogs, etc.).
- Security practices: Threat modeling, fuzzing, audits, formal verification where applicable.
Helpful references:
– Bitcoin whitepaper: https://bitcoin.org/bitcoin.pdf
– Ethereum docs: https://ethereum.org/en/developers/
– Solana docs: https://docs.solana.com/
– Cosmos IBC: https://ibc.cosmos.network/
For Users and Traders: Where Protocols Meet Markets
You don’t need to implement a client to benefit from protocol innovation. Tokens, staking derivatives, and DeFi instruments often reflect the design choices of their underlying protocols. If you trade or invest:
- Understand the protocol’s fee model, token issuance, and roadmap; they influence long‑term value.
- Monitor upgrade timelines (hard forks, EIPs/BIPs), validator distributions, and network health dashboards.
- Use reputable venues and practice robust risk management.
Promo for readers: You can trade major protocol tokens and manage positions on Bybit with code CRYPTONEWER for a 20% fee discount and up to $30,050 in benefits. New to the platform? Create an account through the same link—just remember the referral code is included: Bybit with code CRYPTONEWER.
Note: Promotions are subject to change by the exchange. Read the terms and check your region’s eligibility.
FAQs About Blockchain Protocols
-
Is a blockchain protocol the same as a cryptocurrency?
- Not exactly. A cryptocurrency is a native asset of a blockchain; the protocol is the network’s rule set. You can have multiple assets and applications built on one protocol.
-
What’s the difference between Layer 1 and Layer 2?
- L1 is the base chain (e.g., Ethereum mainnet). L2s inherit L1 security but execute transactions off‑chain (rollups), posting proofs back to L1 for settlement.
-
Who writes and maintains the protocol?
- Core developers and client teams propose changes via improvement proposals. Communities, validators, and sometimes token holders decide to adopt (or reject) upgrades.
-
Can a protocol change without a fork?
- Parameter tweaks may be handled on‑chain, but rule changes typically require coordinated upgrades. Soft forks add restrictions; hard forks change rules in ways that older nodes can’t validate.
-
How do smart contract standards help?
- Standards like ERC‑20 and ERC‑721 ensure wallets, exchanges, and apps can interact consistently with tokens and NFTs across the ecosystem.
-
Are bridges safe?
- Bridges vary. Prefer audited, widely used protocols with robust monitoring. Understand that bridges concentrate risk and can be lucrative targets.
Key Takeaways (Quick Glance)
- A blockchain protocol is the full rulebook for communication, consensus, data structure, execution, incentives, and governance.
- Design choices—PoW vs PoS, EVM vs WASM, L1 vs L2—directly impact security, throughput, and developer experience.
- Interoperability and scalability are evolving fast: rollups, sharding, and DA improvements are reshaping the stack.
- Evaluate networks holistically: cryptography, economics, node diversity, tooling, and governance.
- For trading exposure, use reputable platforms. Perks available via Bybit with code CRYPTONEWER: 20% fee discount and up to $30,050 in benefits.
Disclaimer: This article is educational and not financial advice. Crypto assets are volatile and can be high risk. Always do your own research and consider your risk tolerance before investing or trading.